Summary
On November 3, 2021, the Department of Defense (DoD) issued an Advanced Notice of Proposed Rulemaking (the ANPR) that changes the scope, structure, and roll-out of its Cybersecurity Maturity Model Certification (CMMC) efforts. The CMMC framework has evolved over the past few years and this latest change continues this dynamic trend. In this article, we provide a summary of the ANPR changes to CMMC and the impact on Defense Industrial Base (DIB) companies and discuss how DIB companies can successfully navigate this critical and increasingly dynamic environment.
Background and Overview of the CUI and CMMC Programs
The Cybersecurity Maturity Model Certification (CMMC) is a comprehensive framework used by the Department of Defense (DoD) to enhance cybersecurity and safeguard sensitive national security information in the Defense Industrial Base (DIB). The CMMC traces its origins to Executive Order 13556 which establishes the category of Controlled Unclassified Information (CUI) and to 32 CFR Part 2002 which subsequently established the government-wide CUI program, complete with cybersecurity requirements. The CMMC is the culmination of the DoD’s attempt to protect CUI in its supply chain in line with the Federal CUI final rule (32 CFR 2002).

Date | Order / Rule | Description |
| November 2010 | Executive Order 13556 | An Executive Order is issued by President Obama establishing the CUI classification across all federal agencies and assigning the National Archives and Records Administration (NARA) as the Executive Agent implementing the Order. NARA established the CUI Registry which contains 20 categories of CUI. |
| September 2016 | 32 CFR Part 2002 | The Final CUI Rule is promulgated by NARA which creates the government-wide CUI program and identifies FIPS 200, NIST SP 800-53, and NIST SP 800-171 as integral requirements for the protection of CUI. The rule divides CUI into two categories: (i) CUI Basic; and (ii) CUI Specified. |
| December 2017 | DFARS 252.204-7012 | All contractors were required to have implemented specified requisite controls for “Safeguarding Covered Defense Information and Cyber Incident Reporting” pursuant to the deadline set in a 2015 Interim Rule. The Interim Rule established NIST SP 800-171 as the standard for “adequate security” for Covered Defense Information, including CUI, and established cybersecurity requirements for covered defense contractors. |
| November 2020 | DFARS 252.204-7019, 7020, & 7021 | The DoD promulgated three new rules concerning contractor implementation of CMMC: [1] 7019: Requires assessment of covered contractor implementation of NIST SP 800-171 using the DoD Assessment Methodology to produce a numerical Supplier Performance Risk System (“SPRS”) score. [2] 7020: Defines three levels of assessment: (i) Basic; (ii) Medium; and (iii) High, with basic requiring a self-assessment, and medium and high requiring a government-led assessment. [3] 7021: Establishes the five-level CMMC maturity model with level requirement established in the DoD contract. |
| November 2021 | CMMC 2.0 | An Advanced Notice of Proposed Rulemaking provided insights to CMMC 2.0. The new program will collapse the CMMC framework into three levels to be implemented through two separate rules in Title 32 of the Code of Federal Regulations (CFR) and Title 48 in the Defense Federal Acquisition Regulation Supplement (DFARS).
|
“CMMC 1.0” was established with Defense Federal Acquisition Regulation Supplement (DFARS) Case 2019 – D041, which created an assessment regime to verify that companies holding CUI were meeting baseline cybersecurity requirements. DFARS Clause 252.204-7021 created the CMMC program which planned a phased roll out of contract requirements and created a private sector, third-party assessment regime requiring independent audits with binary results, fully implemented in all DoD contracts by the 4th quarter of 2025. CMMC 1.0 established a robust five-level maturity model based on the control requirements of the NIST SP 800-171 (the standard for protecting CUI since DFARS rule 252.204-7012 in 2017) and modeled on the Carnegie Mellon CMMI process maturity approach.
CMMC 2.0 Requires Slightly Less, but Sooner
In an the ANPR, the DoD indicated several key changes anticipated in CMMC 2.0:
- Removal of CMMC process maturity requirements: While NIST SP 800-171 was always based on an assumed cybersecurity program complete with policies and procedures (FIPS 200 requirements) CMMC 1.0 made these assumptions explicit requirements. These requirements are excised from CMMC 2.0 but remain implicit in 32 CFR 2002 and NIST SP 800-171 which reference policy and procedure requirements from FIPS 200 and NIST SP 800-53. Organizations should expect to need robust policy and procedure documentation to demonstrate compliance to NIST SP 800-171 and CMMC 2.0.
- Removal of CMMC unique controls which were added to the 110 NIST 800-171 baseline controls at the CMMC 1.0 Level 3 and above: The removal of the “Delta Twenty” control requirements lessens some of the implementation burden; however, these twenty controls (email integrity, DNS filtering, backup and recovery, anti-phishing, situational awareness, etc.) are still key parts of a mature cybersecurity program and address the most common vectors of compromise in the DIB.
- Reintroduction of time-bound, enforceable Plans of Action and Milestones (POAMs) for certain requirements: While the POAM is reintroduced, the DoD ANPR suggests that its implementation will be limited to certain types of control requirements and companies will be expected to actually complete remediation activities as a condition of certification/attestation.
- Development of a selective, time-bound waiver process (if approved): Companies may get temporary reprieve from total and immediate implementation; however, it is not yet entirely clear when and how the temporary reprieve will be allowed.
- The removal of levels 2 & 4 which related to no contract requirement: Levels 2 & 4 were defined as “transitional” levels and related to no discrete DoD contract requirement which created ambiguity as to their implementation value for covered contractors.
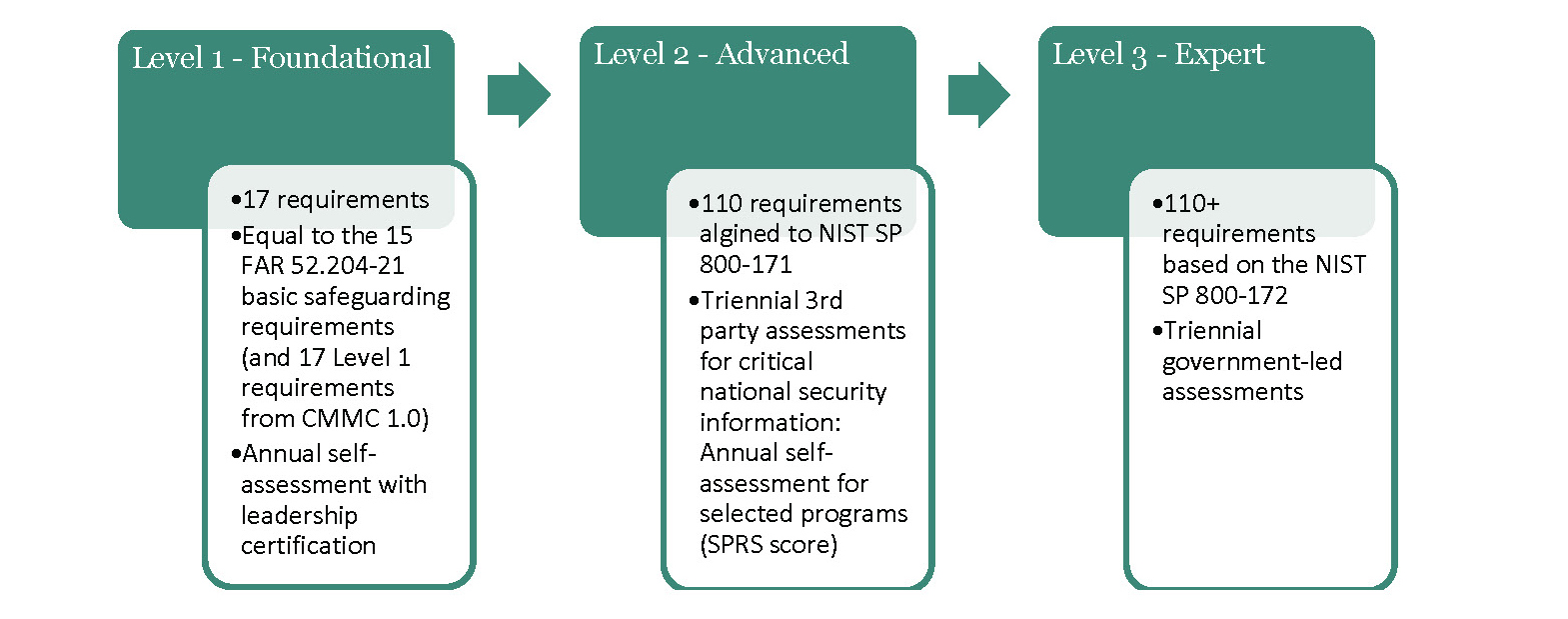
CMMC 2.0 will be implemented in two separate rules, one in Chapter 32 of the Code of Federal Regulations and another in Chapter 48 of the Defense Federal Acquisition Regulation Supplement (DFARS). The Director of CMMC estimated the rule-making process will be complete in 9 to 24 months. At that point, contractors will need to have controls in place for the appropriate level.
Impact to Companies
After the announcement of CMMC 2.0, the DoD suspended the integration of CMMC terms into contracts. However, it will be offering incentives for CMMC certified contractors, which may include increased profit margins and inclusion for consideration in contract awards. Organizations in the DIB should continue to shore up their NIST SP 800-171 implementation, engage in credible independent assessments of their cybersecurity programs, and be prepared to demonstrate implementation of the security requirements of NIST SP 800-171 to their customers in the near future. Regardless of enforcement and verification specifics, CMMC 2.0 will enhance requirements above what is in place today, and likely on a faster timeline than the original CMMC 1.0.
While CMMC continues to evolve, the DoJ continues to push its Civil Cyber-Fraud Initiative with Deputy Attorney General Lisa Monaco announcing that the DoJ is prioritizing enforcement of the False Claims Act. While this has long been applicable to federal contracts generally, DoJ has not specified how this will be enforced for contractors in the CMMC/DFARS 252.204-7012, 7019, and 7020 context. Sub-prime contractors might expect enhanced diligence from prime contractors in the near future. While CMMC 2.0 will require executive signature on attestations, placing personal liability on executives, current contracts contain numerous cybersecurity requirements (FAR 52.204-21 and DFARS 252.204-7012, -7019, and -7020) which require certification of implementation of NIST SP 800-171 among other requirements. While it is important to not overstate enforcement risk, it is incumbent on companies to ensure that any representations and certifications to the government are accurate.
How Ankura Can Help
Ankura’s National Security, Trade & Technology practice is a tight-knit, cross functional team of former prime contractor compliance executives, export control SMEs, cybersecurity professionals, and DIB IT leaders. Ankura’s NSTT team can faciliate the establishment of information technology environments that meet both business objectives as well as a regulatory requirements.
- Strategic Cybersecurity Advisory and Information Security Architecture: Ankura can assist companies by assessing and integrating their regulated data requirements, from FCI to CUI to ITAR, Ankura’s National Security, Trade & Technology provides unrivaled subject matter expertise and tailored solutions to help organizations navigate this rapidly changing business and compliance environment.
- Compliance Assessment, POAMs, and Independent SPRS Analysis: Ankura has deep expertise with the various cybersecurity requirements in the Defense Industrial Base, with specific expertise in meeting NIST SP 800-171 and CMMC implementation requirements. We have conducted numerous assessments and gap analyses to assist clients understand and document their current cybersecurity compliance posture and chart a path to effective cybersecurity governance and execution.
- Policy and Procedure Development and Deployment: Ankura’s bench of senior compliance executives have the expertise to help companies build the governance framework to ensure the credibility and reliability of their cybersecurity implementation. Our experts have assisted clients in the DIB develop and deploy effective, up-to-date policies and procedures that fulfill NIST and CMMC requirements.
- CMMC Self-Attestation and Audit Preparation Support: Whether a company is self-attesting or preparing for an audit, Ankura has former DoJ officials and cybersecurity auditors on the team to address risks and help companies build the assurance case that best protects them and ensures critical lines of business stay open.
- Cybersecurity Incident Response: Ankura has helped numerous clients develop and deploy lean, responsive cyber incident response plans, including development of written incident response plans, design and execution of tabletop exercises, and assistance with live incident response scenarios.

© Copyright 2021. The views expressed herein are those of the author(s) and not necessarily the views of Ankura Consulting Group, LLC., its management, its subsidiaries, its affiliates, or its other professionals. Ankura is not a law firm and cannot provide legal advice.



