On March 15, 2021, President Biden signed into law the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA), which will require critical infrastructure owners and operators (among other things) to report material security incidents within 72 hours and ransomware payments within 24 hours to the Department of Homeland Security’s (DHS) Cybersecurity and Infrastructure Security Agency (CISA).
Background
The CIRCIA requirements respond to several prominent recent cyber-attacks against high profile targets, including (among others): SolarWinds in 2020, Microsoft Exchange in 2021, Colonial Pipeline in 2021, and the remote code execution vulnerability discovered in Apache’s Log4j JavaScript logging library in 2022, which received a 10 out of 10 severity score from the National Institute of Standards and Technology (NIST). The Ukraine conflict also is a catalyst for a stronger U.S. Government focus on cybersecurity, as President Biden has repeatedly warned that “the Russian Government is exploring options for potential cyberattacks.”
While CIRCIA is the first statutory cyber incident reporting requirement specific to critical infrastructure owners and operators, additional U.S. cyber incident reporting requirements apply to other industries:
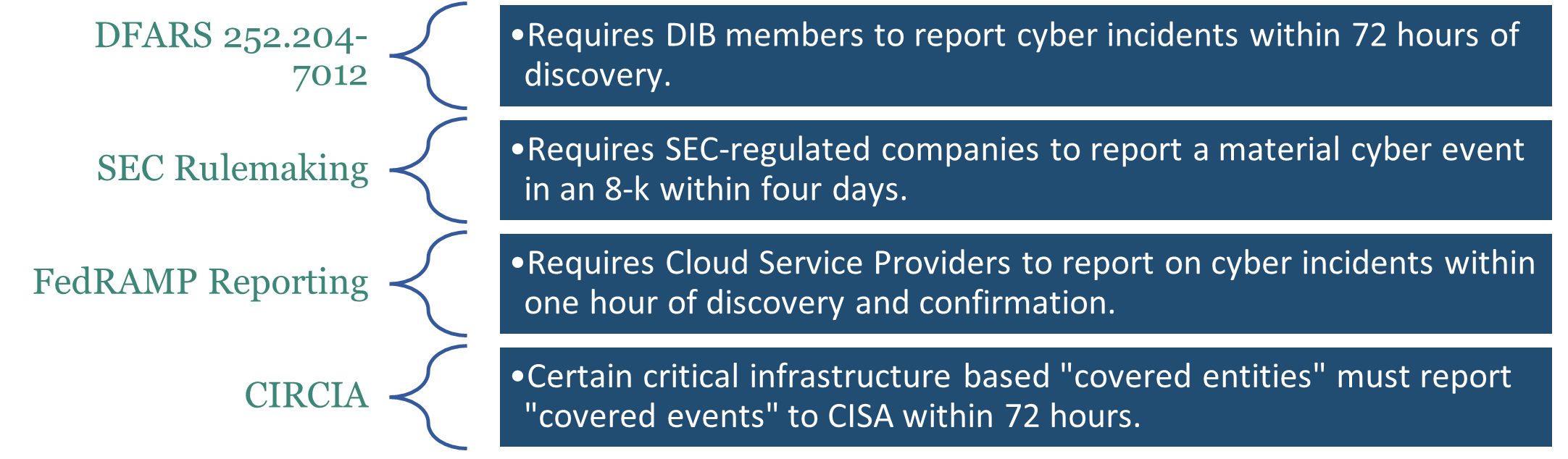
- Defense Industrial Base: The Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.204-7012 requires defense contractors (including subcontractors) to report cyber incidents that affect covered defense information or that affect the contractor’s ability to perform operationally critical support requirements to the DoD’s Defense Cyber Crime Center (DC3) within 72 hours.
- Publicly Traded Companies: On March 9, 2022, the Securities and Exchange Commission (SEC) proposed several rule amendments intended to standardize and enhance required disclosures by publicly traded companies regarding cybersecurity, risk management, strategy, governance, and incident reporting.
- FedRAMP Requirements: Cloud Service Providers operating systems on behalf of federal agencies are required to report suspected and confirmed information security incidents to the U.S. Computer Emergency Readiness Team (U.S.-CERT) within one hour of discovery.
CIRCIA Covered Entities and Incidents
The CIRCIA reporting requirements will become effective when CISA promulgates enabling regulations that specify the subject “covered entities”, which the statute defines as “an entity in a critical infrastructure sector as defined in Presidential Policy Directive 21.” Presidential Policy Directive 21 outlines the following industries as critical infrastructure sectors:
| Chemical | Dams |
| Commercial Facilities | Emergency Services |
| Communications | Energy |
| Critical Manufacturing | Government Facilities |
| Financial Services | Information Technology |
| Defense Industrial Bases | Nuclear Reactors, Materials, & Waste |
| Food & Agriculture | Transportation Systems |
| Healthcare & Public Health | Water & Wastewater Systems |
Under CIRCIA, covered entities are required to report a “covered cyber incident” to CISA no later than 72 hours after the entity reasonably believes that a covered cyber incident has occurred. CIRCIA defines a “covered cyber incident” as one that is “substantial” and meets the “definition and criteria” to be set by CISA in the forthcoming regulations.
In addition to mandatory reporting for covered cyber incidents, covered entities also are directed to report ransomware payments to CISA within 24 hours of making the payment, regardless of whether the underlying ransomware attack is a covered cyber incident. CIRCIA also clarifies that if a covered entity experiences a covered incident and pays a ransom before the 72-hour deadline, the entity may submit a single report to satisfy both reporting requirements.
CIRCIA also empowers CISA with substantial enforcement capabilities. If CISA learns of a non-reported cyber event, it can engage directly with the covered entity to request a report, and if necessary, CISA is authorized to use its newly granted subpoena power. If the covered entity declines to respond or responds inadequately after 72 hours of when CISA requests a response, CISA can refer the entity to the U.S. Department of Justice (DOJ) for a civil action, regulatory enforcement action, or criminal prosecution.
Rulemaking Process
CISA has 24 months to publish a notice of proposed rulemaking and 18 months after that to issue the final rule. While the rulemaking will establish the definition of “covered entities,” CISA must consider certain factors while crafting that definition. These factors include:
- Consequences to “national security, economic security, or public health and safety;”
- Likelihood of attack; and
- Vulnerability of critical roles/operations to attack.
The Rulemaking also will define “covered cyber incidents.” CISA must consider the following factors in creating that definition:
- Only substantial cyber incidents;
- “Substantial loss of confidentiality, integrity, or availability of such information system or network, or a serious impact on the safety and resiliency of operational systems and processes;”
- Effect on business continuity; and
- Third-party risk.
The definition must exclude vulnerability and penetration testing, and “the threat of disruption as extortion, as described in section 2240(14)(A).” Finally, the rulemaking will establish the contents of the report and data preservation requirements.

Impact on Affected Critical Infrastructure Entities
The full scope and implications of CIRCIA will only become apparent after CISA’s rulemaking. But current indicators are that CIRCIA and implementing regulations will significantly impact the critical infrastructure industry and therefore warrant attention from potentially-affected risk management, compliance, and legal leaders. In addition to CISA’s ability to subpoena and refer critical infrastructure owners and operators to DOJ, CIRCIA requires these organizations to report covered cyber incidents, including requirements to:
- Identify and describe the function of the systems, networks, or devices, that were affected;
- Describe the unauthorized access, the estimated data range, and the operational impact of the incident;
- Enumerate the vulnerabilities exploited, tactics used, and the defenses overcome in the incident;
- Provide information about the suspected attacker including information about the ransomware payment where applicable; and
- Biographical information about the covered entity.
A covered entity that pays a ransomware attacker will have to provide the date of the payment, the amount and form of payment requested, and the payment instructions. Moreover, previous rulemaking experience tied to DFARS 252.204-7012 in the DIB context demonstrates that while regulators will consider the burden of compliance on covered entities, national security considerations will tend to dominate their decisions regarding regulatory scope and requirements.
In addition, the mere existence of CISA and the underlying cybersecurity risks it is intended to address already are affecting regulators, industry, and market expectations regarding reasonable behavior. Even before CIRCIA regulations take effect, a critical infrastructure entity that is the target of a cybersecurity incident or ransomware attack runs a significant reputational and legal risk if its response is determined to be lacking.
Accordingly, potentially covered entities should engage early in order to understand and prepare for CIRCIA compliance. Particularly affected parties may consider providing comments during the rulemaking process and enhancing their cybersecurity posture, particularly with respect to identification, reporting, and resolution of cybersecurity and ransomware incidents.
How Ankura Can Help
- Rulemaking Assistance – Ankura’s interdisciplinary team of cybersecurity and incident response experts; former U.S. government policy and national security officials, and in-house compliance and security professionals can help potentially affected organizations to engage with and shape the CIRCIA regulations process by assisting with drafting comments and interacting in the rulemaking process.
- Governance Program Enhancement – Ankura’s holistic approach to cybersecurity implementation is unique in the field. Ankura’s diverse bench of consultants can provide insight into how to create governance structures that can respond to the ever-evolving cybersecurity regulatory landscape.
- Cybersecurity Program Maturity Assessments – Ankura offers an in-depth look at clients’ cybersecurity program maturity through the NIST SP 800-171, NIST SP 800-53, and other prevailing control regimes. These assessments not only help guide organizations through the controls but allow clients to build an assurance case for use in an audit.
- Governance Program Implementation – Ankura has a deep bench of former in-house compliance counsel, federal prosecutors, federal law enforcement, and cybersecurity experts who can work with organizations to identify their regulatory requirements and build a right-sized compliance program.
- Cybersecurity Assessments – Ankura’s extensive experience working with critical infrastructure organizations means that it is well-positioned to conduct credible cybersecurity assessments of companies that fall into one of the categories identified in this legislation. This includes best practices assessments of cybersecurity programs, as well as technical security testing such as vulnerability and penetration tests.
- Incident Response – Ankura’s team brings credible, multidisciplinary expertise in Incident Response and can work with companies to identify, contain, eradicate, and recover from a breach and to ensure that the Incident Response capability meets all the organization’s regulatory requirements.
- Incident Readiness – Ankura’s team works with its clients to adequately prepare for an incident. This includes developing the relevant policies and procedures to respond effectively but also conducting tabletop exercises to test the effectiveness and allow individuals to experience the types of decisions and quick-thinking required when working through an incident.
- Operational Technology Assessment – Operational Technology is a unique area of security, where legitimate expertise is key to ensuring the safety of systems while evaluating and implementing security controls. Ankura personnel have expertise in ICS and SCADA operation and security and are uniquely positioned to advise organizations on how best to integrate regulatory requirements with the reality of their operating environments.

© Copyright 2022. The views expressed herein are those of the author(s) and not necessarily the views of Ankura Consulting Group, LLC., its management, its subsidiaries, its affiliates, or its other professionals. Ankura is not a law firm and cannot provide legal advice.



