On April 28, 2022, the Indian Computer Emergency Response Team (CERT-In), a functional organization under the Ministry of Electronics and Information Technology (MeitY), Government of India issued directions under sub-section (6) of section 70B of the Information Technology Act, 2000 relating to information security practices, procedure, prevention, response and reporting of cyber incidents for Safe & Trusted Internet. [1]
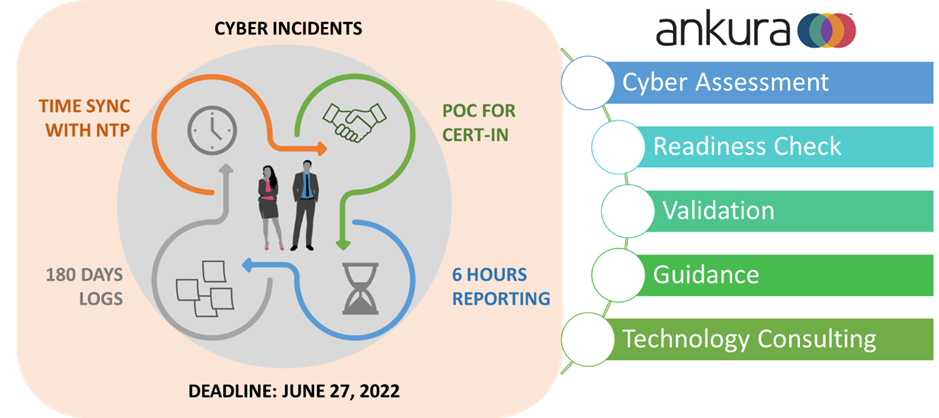
The directions are issued to augment and strengthen cyber security in the country. The directions will be effective from June 27, 2022 (60 days from the date of issue).
- Synchronization of time clocks to NTP servers of NIC - This is applicable to all service providers, intermediaries, data centers, body corporate and government organizations. For the servers and infrastructure hosted in India the time can be synced with the following:
- National Informatics Centre (NIC):
- samay1.nic.in
- samay2.nic.in
- National Physical Laboratory (NPL):
- time.nplindia.org
- National Informatics Centre (NIC):
- For servers and infrastructure outside India the time can be synced with the nearest server having atomic time. You may use https://pool.ntp.org/
- While storing the logs of any device, application, database, etc. make sure the local time as , as well as the UTC time, is recorded in separate columns, if possible, along with time zone details alongside the timestamp.
- Reporting Cyber Incidents in 6 hours to CERT-In - While many other developed countries expect the incidents to be reported in 48-72 hours, CERT-In has given a very aggressive time frame of 6 hours for reporting incidents. This means companies need to have a monitoring mechanism in place to identify cyber security incidents and a well-equipped incident response team along with an incident response plan must be in place. The relevant stakeholders should get immediate intimation in case of a suspected security breach, and they must be in a position to triage and avoid false positives. A readiness assessment can help check if the timeline can be met.
- POC to Interact with CERT-In - Companies will need to assign a Point of Contact with whom CERT-In can communicate for any information. CERT-In has also provided a format in which such information needs to be provided to them.
- Maintaining Logs for 180 Days - All companies need to maintain logs in India for a rolling period of 180 days. This means the companies need to look at their log management policies, logging capabilities of devices and applications, secure log storage, and accessibility. An assessment to validate these points is important for all organizations for ensuring compliance. Companies may have data related to India hosted in overseas data centers, in that case, the logs must be replicated in India.
- It is also important to pass on such obligations to vendors and clients who are handling / storing data so that, in case of a breach, they may be able to comply with the directives.
- Additional obligations for Data Centers, Virtual Private Server (VPS) providers, Cloud Service providers and Virtual Private Network Service (VPN Service) providers:
- Apart from the requirements detailed above, CERT-In has provided a list of data points that needs to be maintained by data centers and server providers for a period of 5 years or more.
- Virtual asset service providers, virtual asset exchange providers, and custodian wallet providers need to maintain KYC details for 5 years.
CERT-in has also provided a list of cyber security incidents and details such as email ID, Phone, and fax number where incidents need to be reported.
With limited time in hand, it is important for companies to relook and validate at their IT infrastructure and logging capabilities so that they are in compliance with the guidelines.
For any further information, please feel free to contact amit.jaju@ankura.com

[1] https://www.cert-in.org.in/Directions70B.jsp
© Copyright 2022. The views expressed herein are those of the author(s) and not necessarily the views of Ankura Consulting Group, LLC., its management, its subsidiaries, its affiliates, or its other professionals. Ankura is not a law firm and cannot provide legal advice.



