ISO (the International Organization for Standardization) and IEC (the International Electrotechnical Commission) have ISO 27000 series which provides requirements for an information security management system (ISMS). They have revised the new information security standard ISO 27002:2022 from the earlier ISO 27002:2013. In the new standard, a new structure and several new controls have been introduced.
What's New?
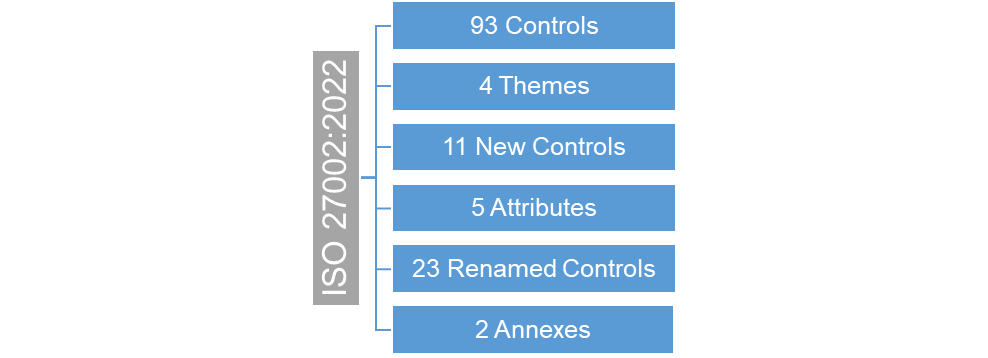
In the new standard, the number of controls have decreased to 93 as a result of removal of few controls, merger of some controls, and addition of 11 new controls.
Control 5.7 - Threat Intelligence
A notable addition to the new standard is Control 5.7, which refers to Threat Intelligence. This covers the need for organizations to collect, analyze, and produce threat intelligence relating to information security threats. In today's environment of an ever-changing threat landscape, cyber threat intelligence allows firms to take preventative measures before an attack begins.
For maximum efficiency, ISO advises three aspects of intelligence.

What Organizations Should Do?
Start by assessing what is relevant for you and comparing the market trends with peers, combined with expert advice and valid, current data sets. Organizations should take a proactive approach by assembling their protection measures before there is a breach.

Relevance for ISO 27001 Certification
No immediate steps need to be undertaken since ISO/IEC 27001 has not been updated so far. But it is important to start reviewing and updating internal controls ahead of the anticipated ISO 27001:2022 update. These guidelines and best practices help better align with the ISO 27001 requirements to get certification. The inclusion of Threat Intelligence highlights its growing importance in ISMS and may set a precedent for other regulations and certifications.
Reactive to Proactive
It’s important to know your threat landscape and act fast accordingly rather than lagging behind patching vulnerabilities letting threat actors exploit them. Threat Intelligence being integral part of organizations’ cyber security efforts help security teams in proactively preparing for upcoming threats.
How Ankura Can Help
Ankura’s Cyber Threat Investigations and Expert Services team has in-depth experience to solve the most mission-critical and complex cyber challenges for clients.
- Ankura’s threat intelligence team leverages many tactics, techniques, and procedures to identify patterns of behavior being used by potential adversarial threat actors.
- A vast amount of anonymized threat intelligence is derived from our daily activities, as we respond to hundreds of cybersecurity incidents per year.
- We design and execute passive intelligence operations, both automated and analyst driven, web-scraping, and archive a multitude of dark web/deep-net forums and sites yielding both current and historic intelligence.
- Our persistent presence in the dark web using surreptitious, backstopped identities enables us to monitor communications in isolated networks and forums.


© Copyright 2022. The views expressed herein are those of the author(s) and not necessarily the views of Ankura Consulting Group, LLC., its management, its subsidiaries, its affiliates, or its other professionals. Ankura is not a law firm and cannot provide legal advice.



